Zerodium Offers $2 Million for Remote iOS jailbreak, $1 Million for WhatsApp RCE
01/09/2019
4042

Zero-day exploit broker Zerodium has raised again the payouts it offers for most desktops/servers and mobile exploits.
A “zero click” iOS remote jailbreak is now priced at $2 million, a WhatsApp, iMessage, or SMS/MMS remote code execution exploit at $1 million, and a local PIN/passcode or Touch ID bypass for Android or iOS at $100,000.
Other major changes to the payouts are shown in this table:
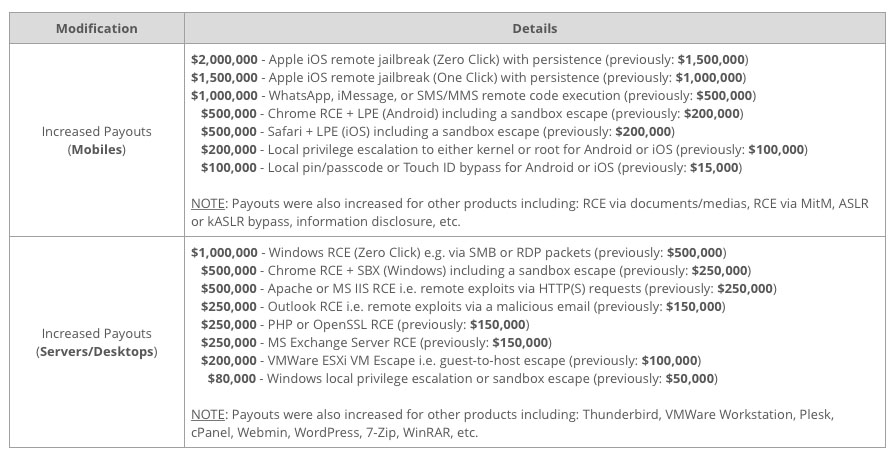
"The company also noted that they may pay even higher rewards for “exceptional exploits and research.”
Buying and selling zero-day exploits
Zerodium was founded in 2015 by Chaouki Bekrar, who previously founded and ran Vupen Security, an infosec outfit that specialized in discovering zero-day vulnerabilities in order to sell them to law enforcement and intelligence agencies.
Zerodium’s business model is different: it acquires zero-day vulnerabilities/exploits from independent security researchers, validates and documents them, then reports them (along with protective measures and security recommendations) to its clients. The company says that a very limited number of vetted, mainly government organizations gets access to the information.
The company is not the only vulnerability/exploit broker out there, but it was the first one that publicly revealed the prices for the various exploits and shared the criteria they use to determine them.
Naturally, high-risk vulnerabilities affecting widely used operating systems and software are the most highly priced. If they come with a reliable exploit that works on most versions, requires no user interaction and can be deployed remotely, the price will reach top level.
Zerodium’s price hike seems to indicate that it’s increasingly difficult to exploit vulnerabilities in some operating systems and applications.
The fact that exploits for individual devices are better priced that those for servers seems to confirm the company’s claim they sell mostly to law enforcement and government agencies (for targeted surveillance). The high prices for messaging app exploits also points to that: breaking their security protections without messing with the rest of the device makes the attackers’ surveillance efforts more difficult to detect, both immediately and in the long run.
Source: helpnetsecurity